Cryptographic Protocol Security Analysis Based On Trusted Freshness: A Comprehensive Guide

In the rapidly evolving digital landscape, the security of cryptographic protocols has become paramount. With the proliferation of online transactions, communication, and data sharing, ensuring the confidentiality, integrity, and authenticity of our digital interactions is crucial. This guide delves into the field of cryptographic protocol security analysis, focusing on the concept of trusted freshness as a fundamental principle for securing protocols.
5 out of 5
| Language | : | English |
| File size | : | 3725 KB |
| Text-to-Speech | : | Enabled |
| Print length | : | 384 pages |
What is Cryptographic Protocol Security?
Cryptographic protocols are sets of rules that govern the exchange of information between two or more parties over a network. They employ cryptographic techniques such as encryption, hashing, and digital signatures to protect the data and provide security guarantees. Protocol security analysis involves examining these protocols to identify potential vulnerabilities and weaknesses that could be exploited by attackers.
The Role of Trusted Freshness
Trusted freshness is a fundamental concept in protocol security. It refers to the ability to ensure that messages or data received from a sender are genuinely fresh, meaning they have not been replayed or modified by an adversary. This is critical for preventing attacks such as replay attacks, man-in-the-middle attacks, and message modification attacks.
Protocol Analysis Techniques
Protocol analysis involves a systematic examination of protocols to identify vulnerabilities. Various techniques are employed, including:
* Formal Methods: Using mathematical models and logical reasoning to analyze protocols for correctness and security flaws. * Model Checking: Employing automated tools to verify protocols against formal models, checking for adherence to security properties. * Attack Simulation: Simulating potential attacks on protocols to identify and exploit vulnerabilities. * Heuristic Analysis: Applying general security principles and domain knowledge to identify potential issues in protocols.
Trusted Freshness Mechanisms
A variety of mechanisms can be employed to achieve trusted freshness in cryptographic protocols, including:
* Sequence Numbers: Using increasing sequence numbers to track the Free Download of messages and detect replayed packets. * Timestamps: Incorporating timestamps into messages to ensure the freshness of data and prevent replay attacks. * Nonces: Generating random numbers that are included in messages to prevent attackers from predicting or replaying messages. * Freshness Oracles: Establishing a trusted third party that provides certificates or tokens to vouch for the freshness of data.
Applications of Protocol Security Analysis
Protocol security analysis is essential for securing various applications and systems, such as:
* Network and Internet Protocols: Ensuring the security of protocols used in network communication, such as TCP/IP, HTTP, and TLS. * Secure Communication Systems: Analyzing protocols used in secure messaging applications, VoIP systems, and video conferencing tools. * Blockchain and Cryptocurrency Protocols: Evaluating the security of protocols underlying blockchain networks and digital currency transactions. * Industrial Control Systems: Safeguarding protocols used in critical infrastructure, such as power grids, manufacturing plants, and transportation systems.
Cryptographic protocol security analysis based on trusted freshness is a vital aspect of cybersecurity. By understanding the concepts, techniques, and mechanisms involved, organizations can effectively identify and mitigate protocol vulnerabilities, ensuring the confidentiality, integrity, and authenticity of their digital communications and systems. This comprehensive guide provides a valuable resource for cybersecurity professionals, network engineers, and anyone who seeks to enhance the security of their digital interactions.
Free Download Your Copy Today!
5 out of 5
| Language | : | English |
| File size | : | 3725 KB |
| Text-to-Speech | : | Enabled |
| Print length | : | 384 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Book
Book Novel
Novel Page
Page Chapter
Chapter Text
Text Story
Story Genre
Genre Reader
Reader Library
Library Paperback
Paperback E-book
E-book Magazine
Magazine Newspaper
Newspaper Paragraph
Paragraph Sentence
Sentence Bookmark
Bookmark Shelf
Shelf Glossary
Glossary Bibliography
Bibliography Foreword
Foreword Preface
Preface Synopsis
Synopsis Annotation
Annotation Footnote
Footnote Manuscript
Manuscript Scroll
Scroll Codex
Codex Tome
Tome Bestseller
Bestseller Classics
Classics Library card
Library card Narrative
Narrative Biography
Biography Autobiography
Autobiography Memoir
Memoir Reference
Reference Encyclopedia
Encyclopedia Sue Kientz
Sue Kientz Sharee Miller
Sharee Miller Ritesh Gupta
Ritesh Gupta Lowell Fryman
Lowell Fryman Rebecca L Hunter
Rebecca L Hunter S L Bridle
S L Bridle W Leydhecker
W Leydhecker Catherine Marshall
Catherine Marshall Robert Joustra
Robert Joustra Mike Rutherford
Mike Rutherford Natalia Andrienko
Natalia Andrienko Michel Gelobter
Michel Gelobter Michael K Chapman
Michael K Chapman Clydell Coates
Clydell Coates Cynthia Rylant
Cynthia Rylant John Hansen
John Hansen Umberto Eco
Umberto Eco Nancy Mcwilliams
Nancy Mcwilliams Laurie Kahn
Laurie Kahn Steven Frank
Steven Frank
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Cason CoxUnveiling the Mind of Parkinson's: A Comprehensive Guide to Understanding and...
Cason CoxUnveiling the Mind of Parkinson's: A Comprehensive Guide to Understanding and...
 Tyler NelsonMother and Child: The Well Woman - A Comprehensive Guide to Pregnancy, Birth,...
Tyler NelsonMother and Child: The Well Woman - A Comprehensive Guide to Pregnancy, Birth,...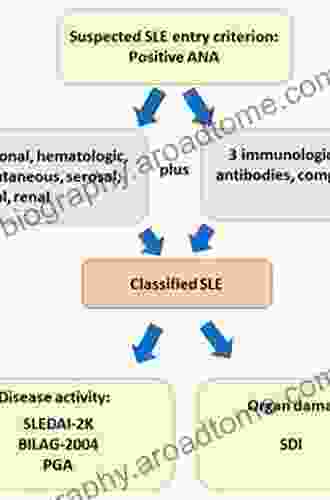
 Leslie CarterLupus Erythematosus: Clinical Evaluation And Treatment: A Comprehensive Guide...
Leslie CarterLupus Erythematosus: Clinical Evaluation And Treatment: A Comprehensive Guide... Tyler NelsonFollow ·4.8k
Tyler NelsonFollow ·4.8k Virginia WoolfFollow ·9.6k
Virginia WoolfFollow ·9.6k Ronald SimmonsFollow ·18.4k
Ronald SimmonsFollow ·18.4k Quentin PowellFollow ·15.6k
Quentin PowellFollow ·15.6k Raymond ChandlerFollow ·11k
Raymond ChandlerFollow ·11k Aubrey BlairFollow ·10.9k
Aubrey BlairFollow ·10.9k Griffin MitchellFollow ·13.9k
Griffin MitchellFollow ·13.9k Dakota PowellFollow ·13.3k
Dakota PowellFollow ·13.3k
 Ashton Reed
Ashton ReedUnveiling the Silent Pandemic: Bacterial Infections and...
Bacterial infections represent...

 Brent Foster
Brent FosterFinally, Outcome Measurement Strategies Anyone Can...
In today's...

 Brett Simmons
Brett SimmonsUnlocking the Secrets to Entrepreneurial Excellence:...
Empowering...

 Eugene Powell
Eugene PowellOur Search For Uncle Kev: An Unforgettable Journey...
Prepare to be captivated by...
5 out of 5
| Language | : | English |
| File size | : | 3725 KB |
| Text-to-Speech | : | Enabled |
| Print length | : | 384 pages |